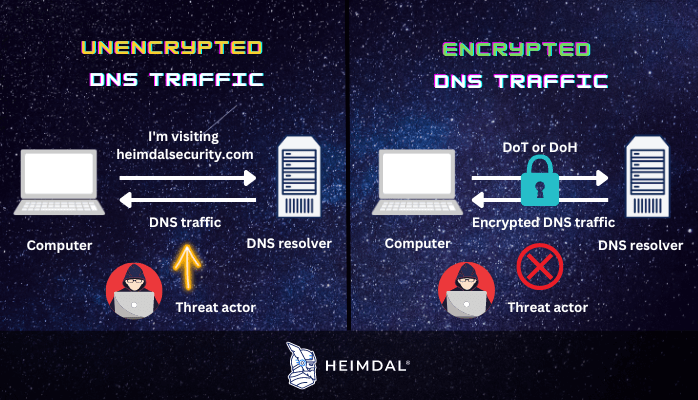
Encrypted DNS traffic is a type of DNS traffic secured in a way that no third party can intervene during a DNS resolution (the process of translating a domain name into an IP address). This means that no one can intercept the data changed during a DNS request, so the names of the websites and servers you access are safe from possible eavesdroppers.
In this article, we will explore how encrypted DNS traffic works, what types of encryption are most used in the present, and why encrypting DNS traffic is so important to keep you and your organization safe against cyberattacks.
Why encrypt DNS traffic?
Without encryption, between your device and the DNS resolver, anyone can look at or change your DNS queries and responses. This includes anyone on your local Wi-Fi network, your Internet Service Provider (ISP), and transit providers. This could hurt your privacy by letting people know what domain names you are visiting.
Encryption has always been about making sure browsing the internet is safe and private. On a small scale, knowing that someone queried ‘heimdalsecurity.com’ isn’t that terrible, but on a bigger scale, it could mean that an organization could determine the online habits of a person, interests, and sometimes intent. These insights might then be sold to other organizations for profit, or used by threat actors to perform financial fraud.
72% of enterprises have been the target of at least one DNS attack in the past year, and in 58% of those instances, the impact was substantial, according to a study conducted by Neustar International Security Council in 2021. With DNS attacks on the rise, encrypted DNS traffic appeared as a solution against any spying, spoofing, man-in-the-middle, or other types of DNS attacks.
How does encrypted DNS traffic work?
Encrypted DNS traffic works by converting plain text DNS information into an encrypted version that can only be deciphered by the parties engaged in the communication, namely the DNS client (your browsers, network devices, etc.) and the DNS resolver.
Types of DNS encryption
DNS was not created with security in mind because the internet was still in its earliest years when DNS was initially launched, and there were no online businesses, banking, or e-commerce websites, so there was really no need to encrypt DNS traffic. Almost four decades later, fast forward to the present, with e-businesses booming and cybercrime increasing, two protocols were developed to perform DNS encryption: DNS over TLS (DoT) and DNS over HTTPS(DoH).
DNS over TLS (DoT)
DNS over TLS (DoT) is a network security protocol that uses the Transport Layer Security (TLS) protocol to encrypt and wrap DNS queries and answers. TLS, which is used by HTTPS websites for encryption and authentication, is also used by DoT. (“SSL” is short for “Transport Layer Security,” which is another name for TLS). For DNS queries, DoT builds on top of the user datagram protocol (UDP) with TLS encryption.
The goal of this method is to give users more privacy and security by stopping man-in-the-middle attacks that may otherwise be used to snoop on or alter DNS traffic. Among Internet users, the most common port used for DoT is port 853.
DoT protocol supporters argue that the DNS over TLS standard is more suited to address human rights issues in challenging jurisdictions. However, in nations where freedom of speech is restricted, enabling DoT encryption may have no effect beyond drawing attention to the issue. To put it another way, those who choose DoT over the more conventional DoH may be met with hostility from authoritarian regimes.
DNS over HTTPS (DoH)
DNS over HTTPS is a protocol that uses HTTPS(Hypertext Transfer Protocol Secure) to perform remote DNS resolution. This protocol operates through port 443 – which is currently the industry standard for all HTTPS connections. Resolvers (DoH clients) must be able to connect to a DoH server that hosts a query endpoint.
DoH in Google Chrome
In version 83 of Google Chrome for Windows and macOS, DNS over HTTPS is supported and can be enabled from the browser’s options page. If you enable this feature and your operating system is set up to use a compatible DNS server, Chrome will upgrade DNS requests to use encrypted communication. The user interface also allows for the selection of a default or user-defined DoH server. Google Chrome for Android also launched a phased release of DNS over HTTPS in September 2020. In settings, users can configure a custom resolver or disable DNS over HTTPS.
Chrome is preconfigured with five DNS over HTTPS providers, including Google Public DNS, Cloudflare, Quad, CleanBrowsing, and NextDNS.
DoH in Microsoft Edge
DNS over HTTPS is also supported in Microsoft Edge and can be configured in the browser’s settings. When enabled and a compatible DNS server is specified in the operating system, Edge will enable all DNS queries to be encrypted. Using the interface, users may also choose between using a default DoH server or creating their own.
DoH in Mozilla Firefox
Cloudflare and Mozilla formed a partnership in 2018 to provide DoH for Firefox (known as Trusted Recursive Resolver). Since February 25, 2020, all Firefox users in the United States have been be able to use DNS over HTTPS, with Cloudflare’s resolver serving as the default.
DoH in Opera
DoH is supported by Opera and can be enabled or disabled in the browser’s preferences. DNS requests are automatically directed to Cloudflare’s servers.
DoH in Operating Systems
The operating system (OS) industry has been one of the last to embrace new technologies, but that is beginning to change. In Windows 10, you can enable DNS over HTTPS in the Settings menu. If you’re on Windows 10 Version 1805 or later, head to the Settings > Network & Internet menu. My colleague Miriam wrote an extensive article on how to enable DoH in Windows 10 and the pros and cons of using this protocol.
Apple has also recently expanded its alterations to incorporate new app-level encryption techniques. This means that from now on, app developers can use their own encrypted DNS configurations when building their apps, rendering your controls unnecessary (a great example of this is TikTok).
How Can Heimdal® Help?
With DNS over HTTPS (DoH) and Hybrid DNS, Heimdal® has added, as of September 15th, two brand-new, industry-defining capabilities to its core DNS security. While the latter is now part of the Threat Prevention Network, the former has been included in the Threat Prevention Endpoint solution.
With this product update, Heimdal® becomes the only vendor to support full DNS over HTTPS filtering, which goes beyond the conventional way of rerouting DNS packages.
DNS over HTTPS is here to protect your IT environment from DNS spoofing and Man-in-the-middle (MitM) attacks by encrypting the session between your browser and DNS server. This makes it harder for threat actors or third parties to change the results of a resolution request, keeping them from sending the user’s browser to an infected website.
By adding DoH to the Threat Prevention Endpoint, Heimdal® makes it possible for organizations to stay one step ahead of the game and use the Internet in a safer and more private way. All DNS queries are sent through a Hypertext Transfer Protocol Secure encrypted session, which encrypts the domain name system traffic.

Antivirus is no longer enough to keep an organization’s systems secure.
Heimdal® Threat Prevention
– Endpoint
Is our next gen proactive shield that stops unknown
threats before they reach your system.
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
Wrapping up
Using encrypted DNS traffic is a great way to upgrade your privacy and security when browsing the internet. Just keep in mind that, no matter what type of DNS encryption you pick, it is safer than having no encryption at all. A proper DNS traffic filtering system can always keep you and your organization safe from DNS attacks and help you save valuable resources.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.








