The last few years have been truly transformational, and as 2023 approaches, you may be wondering what will happen next in terms of cybersecurity. I’m confident that this year will be a game changer, with cyberattacks on the rise and revolutionary cybersecurity products entering the market. Here are more details!
Top Cybersecurity Trends to Be Aware Of in 2023
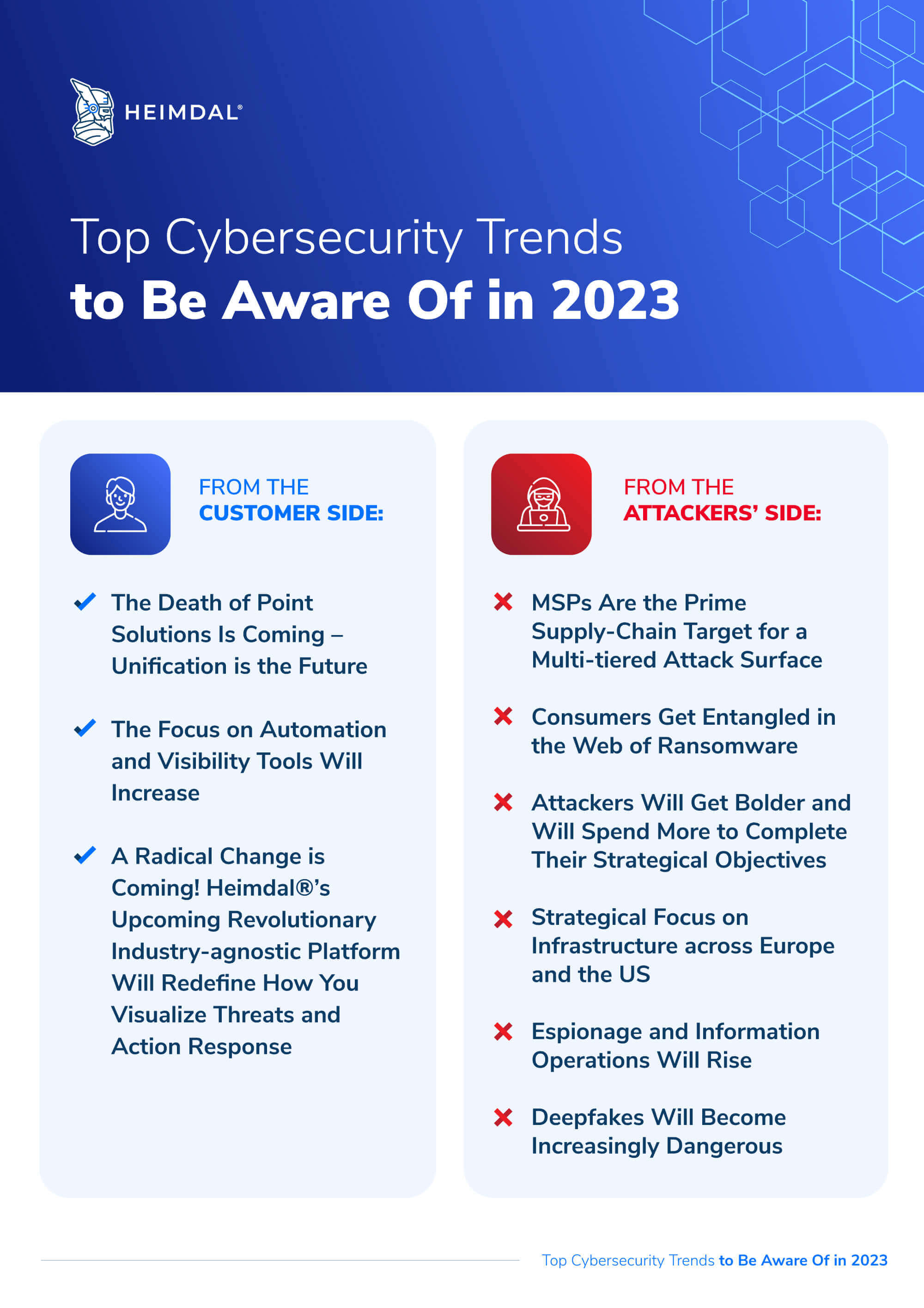
From the customer side:
1. The Death of Point Solutions Is Coming – Unification is the Future
Today’s CISOs and other decision-makers place a strong emphasis on centralized architectures that provide prevention, detection, and mitigation under a single roof in order to increase visibility and efficiency.
With outdated point solutions created in a time when the cyber security landscape didn’t present as many threats and a talent shortage, organizations will keep turning to centralized solutions to meet the high demands of the IT threat landscape.
2. The Focus on Automation and Visibility Tools Will Increase
Automation is here to stay. The causes are numerous and really quite easy to grasp. Security systems generate almost infinite amounts of data, which no team could handle in real-time and react to in a timely manner. The cyber threatscape simply evolves too fast. There is a severe shortage of skilled cybersecurity professionals (and even those currently in the market are exposed to one of the most dangerous risks in the industry – human error). Moreover, hackers are using automation too!
To move from reactive to proactive security and regain control over one’s environment and schedule, analytics, intelligence, and automation are essential. In the corporate IT environment, security automation can identify potential threats, assess the event to determine whether it is real or fake, and then contain and eliminate the threat. Without human assistance, automated security tools complete these actions in a matter of seconds.
Cybersecurity automation minimizes security teams’ alert fatigue by examining alerts, identifying threats, and reducing the effects of attacks.
3. A Radical Change is Coming! How You Visualize Threats and Action Response Will Be Redefined with Heimdal®’s Revolutionary Industry-agnostic Platform
With this addition to the lineup, Heimdal is creating a new category in the cybersecurity market by providing a new approach to Security Orchestration, Automation and Response (SOAR), and Security Information and Event Management (SIEM) technology and engineering.
Heimdal’s Threat-hunting & Action Center was developed in response to an ever-changing threat environment where IT teams’ time and resources were being stretched thin across a huge spectrum of priorities.
The platform solves the need for a plethora of solutions that end up creating a slow and inefficient environment by combining everything into a single unified, integrated, and AI-driven solution that will forever change the way you think about cybersecurity.
From the attackers’ side:
4. MSPs are the Prime Supply-Chain Target for a Multi-tiered Attack Surface
In line with last year’s prediction, we also predict a heavy increase in supply chain attacks in 2023. Attacks on the software supply chain take place when a malicious actor gains access to an MSP or a software vendor’s network and compromises the software before the vendor distributes it to customers. The sharp rise in software supply chain attacks is partly due to the accelerated business climate, which has resulted in less time for MSPs to react and rapid software release cycles from vendors, leaving developers with less time to identify and address security flaws.
With the rapid increase in IT outsourcing, MSPs in particular are a ripe target for cybercriminals.
This leads, naturally, to a multi-tiered attack surface, that can severely compromise customer data and IT systems. Attacks on the software supply chain increased by more than 300% in 2021 compared to 2020, and I predict that they will increase even more in 2023.
The fact that NIST has released a thorough guide on how institutions can defend themselves against supply chain attacks and compromise and the numerous 2022 news (see details about US newspapers, Oktapus, Comm100 Live Chat application) regarding supply chain attacks are clear signs of how serious this threat is.
5. Consumers Get Entangled in the Web of Ransomware
Cybercriminals will successfully compromise internet-based software delivery services, such as Steam, Halo, Blizzard or others, to deliver a hypercomplex ransomware attack through system rights provided by the services. Supply chain attacks will therefore no longer be just B2B-based, but expand the attack sphere into the consumer space for a mass-based exploit-to-ransomware payout attack.
6. Attackers Will Get Bolder and Will Spend More to Complete Their Strategical Objectives
Cybersecurity criminals have plenty of time and plenty of resources to complete their attacks and therefore they will surgically target big institutions to find a way through their defenses.
Attacks of this caliber will typically run into tens of thousands of dollars per month, as cybercriminals use resources in less developed countries, or could be state-backed from North Korea, Russia, China, Iran or similar. They will need to be numerous because even for orchestrated attacks, success is never guaranteed, but when the reward is in the tens of millions of dollars, the cost becomes insignificant.
7. Strategical Focus on Infrastructure across Europe and the US
Transport, energy, and other examples of critical infrastructure are becoming more complex and dependent on networks of interconnected devices. Therefore, unsurprisingly, a major concern today is the critical infrastructure’s susceptibility to technical failures and cyberattacks. Recent occurrences like the war between Russia and Ukraine have only fueled these fears.
State and non-state actors now have more technical know-how, motivations, and financial resources than ever before to destabilize a nation’s vital infrastructure. An attack on vital infrastructure in one region of a nation can have a significant negative impact on many others – the most recent cyberattack on DSB demonstrated exactly how an online threat on a third-party IT service provider can cause serious disruption in the real world.
I believe we will see many cybercriminals adopting this route in 2023.
8. Espionage and Information Operations Will Rise
Information operations and cyber espionage will likely increase. Iran, China, and Russia, the usual actors in information operations, will probably continue to promote narratives that best serve their objectives.
Additionally, they will highlight the idea that the United States failed to honor its obligations to international organizations and nations.
We can already see that the Russian invasion of Ukraine is partially supported by a cyber strategy that entails at least three separate, occasionally coordinated processes: destructive cyberattacks inside Ukraine, network penetration and espionage in other states, and cyber-influence operations aimed at people all over the world.
9. Deepfakes will become increasingly dangerous
Deepfake technology manipulates existing or brand-new audio and video content using artificial intelligence techniques. Although it can be used for legitimate purposes — satire and gaming, for example —, it can also, just like everything else, be misused by malicious actors for malicious purposes.
Deepfakes are used to fabricate a story that seems to come from reliable sources. The two main threats are against civil society (disseminating false information to influence public opinion in a particular direction) and against people or businesses so that malicious actors can make a profit.
The path to a dystopian future will be guaranteed if people will no longer be able to distinguish between truth and lies.
Deepfakes pose a significant cybersecurity threat to businesses because they could make phishing and BEC attacks more successful, make identity fraud much simpler, and significantly reduce share value by twisting brand reputation.
Heimdal’s Predictions for 2022 – Brief Overview
Last year I predicted that:
1. Supply Chain Attacks – Ransomware Especially – Will Keep Their Title as the Biggest Threat for Any Company on the Globe
In 2021, in terms of ransomware, I was concerned about intermittent encryption and double extortion ransomware. However, in 2022, we’ve seen the rise of another ransomware technique.
As Scott Sayce, Global Head of Cyber at AGCS, mentions,
The cost of ransomware attacks has increased as criminals have targeted larger companies, critical infrastructure, and supply chains. Criminals have honed their tactics to extort more money. Double and triple extortion attacks are now the norm – besides the encryption of systems, sensitive data is increasingly stolen and used as leverage for extortion demands to business partners, suppliers, or customers.
Intermittent or partial encryption is a relatively new technique that allows threat actors to avoid detection and corrupt victims’ files faster.
Intermittent encryption has recently become increasingly popular among ransomware operators, who extensively promote the functionality in order to attract clients or partners.
In a double extortion ransomware attack, the data is first exfiltrated, then encrypted, so if the victims refuse to pay the ransom, it will be leaked online or even sold to the highest bidder. Maze, Egregor, Sodinokibi, and Nefilim are just a few examples of ransomware whose operators use(d) this tactic.
In a triple extortion ransomware attack, criminals demand money not only from the first target organization but also from anyone who might be endangered if that organization’s data is made public. Other attacks may be launched against the initial target if they refuse to pay the ransom.
Heimdal’s own revolutionary Ransomware Encryption Protection software issued a total number of 1.4 million alerts and blocked 11.600 processes in the last 3 months – compared to 8738 detected and stopped processes in 2021.
2. Remote Work Challenges Will Keep Accelerating at a Whirling Rate
I anticipated that the most pressing remote work challenges in 2022 would be related to aspects such as IoT, BYOD, and cloud security, as well as email threats such as phishing.
Since the pandemic started and employees began working remotely, the vast majority of businesses have seen a significant increase in cyberattacks.
According to GAT Labs, 66% of security breaches are the result of employee negligence or malicious behavior, whereas 82% of employers report a deficiency of cybersecurity skills.
3. Data Protection Will Have a Massive Impact on Authentication Evolution
In 2021 I was saying that in 2022 passwords will be combined with other authentication methods like smart cards, three-factor authentication, and biometrics in order to improve security, but also user experience.
Current trends indicate that the future is actually passwordless, with passwords being replaced by authentication methods that use Knowledge Factors (something you know), Possession Factors (something you own), and Biometric Factors (something you are).
4. Machine-Learning and Artificial Intelligence Will Be Real Game Changers in the Evolution towards Prevention Instead of Mitigation
AI and machine learning play a major role in making cybersecurity solutions more effective and more practical, helping companies anticipate threats and actually respond to them in real-time. The alert-to-response ratio can easily overwhelm many in-house security teams as cyber expertise declines. Utilizing AI enables overloaded teams to scale up security services and automate and coordinate advanced response actions.
5. Real-Time Data Visibility Will Be Elementary for Any Cybersecurity Software
As is the case of automation, artificial intelligence, and machine learning, real-time data visibility has begun to be a core component of any good cybersecurity solution on the market.
Presently, a large number of cybersecurity firms that provide real-time data solutions transfer the information they have gathered onto maps that change as the situation does. Some of them display the frequency of various types of cyberattacks by geographic location. Some disclose the locations of servers that are used to carry out cybercrimes.
Heimdal as well has been enhancing real-time data visibility within a new product that will be added to our portfolio, which will empower security leaders and teams with an advanced threat-centric view of their entire IT landscape.
6. Extended Detection and Response and Unification Will Be Front-Page Aspects of Any Cybersecurity Strategy
XDR brings a cross-layered detection and response approach, improving security by looking at endpoints, servers, clouds, networks, and email agents, and enhancing productivity while substantially reducing costs.
Unified endpoint management is also crucial for an effective cybersecurity strategy, enhancing productivity and reducing costs, offering the much-needed real-time data visibility that all company owners must have at any time
Businesses are moving toward greater integration and fewer consoles. Gartner also expects that “By 2025, 80% of enterprises will have adopted a strategy to unify web, cloud services and private application access from a single vendor’s security service edge (SSE) platform” and that “By 2027, 50% of midmarket security buyers will leverage eXtended detection and response (XDR) to drive consolidation of workspace security technologies, such as endpoint, cloud and identity.”
7. Cybersecurity Awareness Will Have Fantastic Growth among Both Home Users and Professionals
Having an idea about what could go wrong in terms of cybersecurity and being curious about what can be done to avoid problems are the first steps of prevention. Among employees, cybersecurity awareness training significantly reduces the risk of becoming the target for phishing and ransomware attacks, and it has proven to be essential for any powerful cybersecurity strategy.
Stay Ahead of Current and Future Threats with Heimdal®
A dashboard that integrates intelligence from several or all of Heimdal’s solutions and is highly customizable to meet the needs of each client is the foundation of Heimdal’s unique market positioning. With Heimdal’s unified platform, IT managers, CIOs, and CISOs can monitor their organizations’ cybersecurity state, and manage and respond to threats as swiftly as possible.
Our portfolio stands out for DNS security, Patch and Asset Management, Ransomware Encryption Protection, and Privilege Access Management (Privilege Elevation and Delegation Management in particular), but we also tie these into Antivirus, Application Control, Email Security, and Email Fraud Prevention for added value.
The upcoming Heimdal Threat-hunting & Action Center, which will be available in early 2023, will provide security leaders and teams with an advanced threat-centric view of their entire IT landscape, and granular telemetry to enable rapid decision-making using built-in hunting and remediation capabilities.
Although the cybersecurity landscape is ever-changing, Heimdal’s solutions and cybersecurity strategy can help you always be one step ahead of cybercriminals.

Final Thoughts
2023 will most likely be just as challenging as the previous few years, but I’m confident that the cybersecurity market has the right tools to deal with the constantly shifting cybercrime landscape and new/consolidated threats, whether we’re talking about supply chain attacks, ransomware, deepfakes or cyber espionage.








