Identity Governance and Administration, also known as IGA in cybersecurity or identity security, is a strategic approach to security that aims to help companies reduce cyber risk, manage digital identities and access privileges, and comply with government regulations to secure sensitive information.
Thanks to Identity Governance and Administration, sys admins have better visibility into identities and access privileges and can implement the necessary controls to thwart unauthorized or dangerous access. So basically, in order to prevent data breaches, they ensure that the right users have access only to the information they need.
Components of Identity Governance and Administration
As the name implies, IGA combines Identity Governance and Identity Administration:
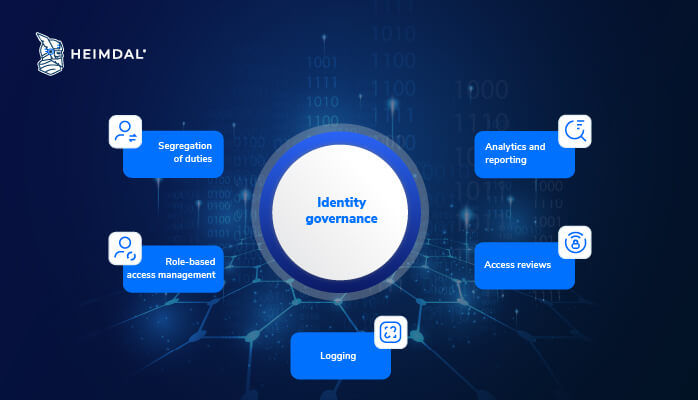
Identity governance
Is all about visibility. It includes procedures and guidelines for the segregation of duties, role-based access management, logging, access reviews, analytics & reporting in order to provide organizations with an accurate and deep understanding of access privileges, as well as different tools for detecting unusual activity.
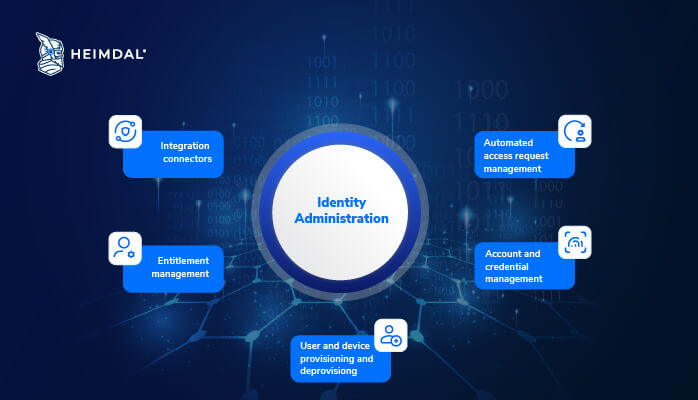
Identity administration
It includes elements like integration connectors, entitlement management, user and device provisioning and deprovisioning, account and credential management, and automated access request management.
The combination of the two boosts compliance and lowers the risk by enabling capabilities that go beyond the scope of conventional Identity and Access Management (IAM) technologies.
Why Is It Important for Companies?
Identity Governance and Administration security’s value was first acknowledged in 2012 when the world’s leading information technology research and advisory company Gartner said it is the fastest-growing sector in the identity and access management market.
In the corporate world, growing digitization translates to more devices, users, and information across on-premises and multi-cloud or remote environments. Hence, sometimes it is challenging to successfully manage user identities and access in such intricate IT security settings. When users are granted unrestricted or unnecessary access to computer systems, apps, or data, security risks increase, the volume of cyber threats also increases, and the organization becomes vulnerable to cyberattacks and data breaches.
By using IGA solutions, as part of the cloud governance approach, IT teams can monitor and manage user access for both on-premises and cloud-based systems. They can protect users by making sure that the right user accounts can access the right systems and identify and stop unauthorized access. Organizations can reduce risk and keep up with regulatory compliance by putting the right controls in place with Identity Governance and Administration.
IGA vs IAM
Many people are unsure about the distinction between Identity and Access Management and Identity Governance and Administration due to the overlap in identity, access-based, and governance solutions. So, let’s take a look at it.
Identity Governance and Administration (IGA) is an important part of a powerful Identity and Access Management (IAM) solution. Nevertheless, IGA solutions offer additional features beyond conventional IAM systems and help in tackling common IAM issues. Some of these challenges are:
- unauthorized and/or out-of-date access to corporate assets
- remote workforce,
- long and complex provisioning and deprovisioning processes
- inadequate Bring Your Own Device (BYOD) policies,
- rigorous compliance requirements.
These challenges exacerbate the security risk and weaken companies’ compliance posture. However, organizations can address them by enhancing their identity management systems with an Identity Governance and Administration solution.
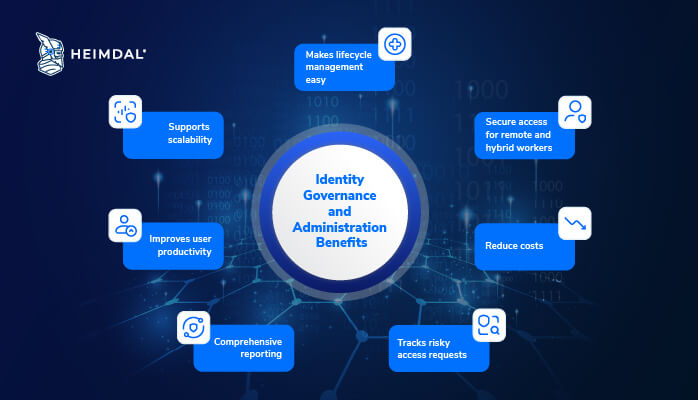
Benefits of Identity Governance and Administration (IGA)
Identity lifecycle management made easy
As user roles or responsibilities within the organization change, because an employee may move to a different department or leave the company, access permissions also change. An Identity Governance and Administration solution make it easy to manage all these changes, from provisioning to de-provisioning. Employee onboarding and offboarding are basically effortless thanks to automation. By managing passwords, permissions, and access requests, such solutions also help maintain control over IT resources such as users, devices, and networks.
Secures access for remote and hybrid workers
Employees can access applications and data from multiple devices at any time, regardless of where they are with advanced authentication processes that use Multi-factor Authentication (MFA) to improve security. This way, companies stay flexible and employees work more effectively.
Cost cutting
Identity Governance and Administration automates labor-intensive operations like access certifications, access requests, password management, and provisioning, resulting in significant cost savings. This can dramatically reduce the time IT professionals spend on administrative work while also empowering users to request access, manage passwords, and review access independently.
Tracks risky access requests
An IGA system offers a centralized location for approvals, making it simple for users to request the access they need to complete their tasks. Thanks to centralization, administrators can control permissions, monitor and detect unusual activity and stop potential malicious actors from gaining access to corporate systems or data.
Comprehensive reporting for better security and compliance
Due to the detailed reports and data analysis, IT administrators are able to better understand what’s happening across the corporate environment and detect issues or threats faster. They can then try and fix problems to safeguard resources that are crucial for business operations. As previously mentioned, data centralization also enables administrators to go through access reports to meet compliance requirements.
Improves user productivity
Strong IGA solutions enable companies to safely grant and manage remote access in order to maintain business continuity and prevent breaches from happening. This way, employees can work from anywhere they want and thus boost productivity and performance. Additionally, automated processes save time and free up employees to focus on more vital areas where they get more work done with fewer resources.
Supports scalability
Identity Governance and Administration solutions support centralized policies and automated processes that help lower operational costs, make sure that workers have access to the data they need, minimize threats, and boost compliance. All of these advantages enable enterprises to scale organically, which they wouldn’t be able to do with manual processes or reduced visibility into users, identities, and systems.
How to Choose the Right Solution for Your Business
The right IGA solution helps a company to overcome existing threats and challenges while also helping it to scale into the future. With that in mind, consider technologies that can:
Make data easy to understand
Implement technology that reduces the reliance of IT stakeholders on manual analysis. Making decisions is easier and more control is ensured when having an uncomplicated governance program with understandable data.
Have a risk-based strategy
Systems should be using risk-based decision-making for user privileges to reduce the accrual of access privileges after a project is completed or when an individual leaves the company.
Implement least-privilege access
Within applications, it guarantees that employees can access only the resources they need to complete their tasks and that their access is constantly verified (a cybersecurity practice known as the Principle of Least privilege or POLP). Just-in-time provisioning can assist in removing standing privileges, which give users permanent access to systems or data and put organizations at risk.
How to Implement Identity Governance and Administration?
Even though most organizations would benefit greatly from an IGA solution, its implementation can be challenging and time-consuming. Here are 5 steps to get you started:
Step 1. Analyze current IGA processes to comprehend identity governance and administration issues that frequently bother customers. Start the process by listing challenges, necessary skills, and stakeholders to address them.
Step 2. Prioritize security objectives based on the potential threats to the business, but strike a balance between urgent needs and a product’s long-term ability to integrate with other tools as a component of an ecosystem.
Step 3. Be specific regarding the architecture and connectors required to protect the environment and scale those solutions into the future. Analyze the relationship between Identity Governance and Administration systems and the existing platforms, and take into account the ease of implementation and use.
Step 4: Start the journey with new features and applications that offer visible improvements quickly, like automated onboarding and offboarding.
Stef 5: Provide training for your staff on solutions so that people can look for situations where remediation might be helpful.
Step 6: Because Identity Governance and Administration is a constant necessity for businesses, changes in the corporate climate, available technologies, and regulatory environment all require an ongoing reassessment of implementation. Furthermore, improved analytics and reporting from the initial implementation can help with the identification of new risk areas.
Common Questions
Are IGA solutions available only on-premises?
As was the case with numerous other technologies, identity governance solutions were initially built on-premises, but they have since mostly transferred to the cloud. Examples of cloud-based services include provisioning, password management, access certifications, and access requests.
Do businesses that don’t have to comply with regulatory compliances need Identity Governance and Administration?
Yes. Any cybersecurity strategy must include identity governance. As malicious actors are always on the lookout for user credentials to steal, it’s crucial that companies take all the necessary steps to prevent unauthorized access to their corporate systems. Whether or not an organization has to comply with regulations, it must secure user accounts and privileges and make sure they have efficient access controls.
Is Identity Governance and Administration the same as Identity Access Management?
Nope. While the two systems go hand in hand, they’re not the same thing. An IGA solution goes beyond traditional IAM processes by helping organizations with identity management, meeting regulatory requirements, and auditing procedures for compliance reporting.
Is IGA relevant to small businesses or large organizations?
Is relevant to all organizations. No matter the size of your company, managing access controls and having a solid process in place for controlling access to your systems is pivotal. For small companies wanting to scale and expand their customer base, using an IGA system can guarantee that they are proactively in compliance with regulations.
Wrapping Up…
An Identity Governance and Administration approach help ease the IT team’s burden by enabling the organization to automate processes that include access requests by role and manage bulk approvals. Regardless of the size of your company, it’s essential to acknowledge the importance of cybersecurity and be aware of the risk of breaches caused by gaps between erroneous access and security concerns.
In a nutshell, this types of solutions aid organizations in minimizing risks, improving their identity access management, boosting compliance and audit performance, increasing productivity and efficiency, and cutting costs.
What Does Heimdal® Bring to the Access Management Market?
When it comes to access management, Heimdal puts on the table one of the best solutions in the market: Privileged Access Management (PAM).
Heimdal® Privileged Access Management allows system administrators to manage user permissions easily. Your system admins will be able to approve or deny user requests from anywhere or set up an automated flow from the centralized dashboard. Furthermore, Heimdal Privileged Access Management is the only PAM solution on the market that automatically de-escalates on threat detection.
Managing user permissions and their access levels is not only a matter of saving the time of your employees but a crucial cybersecurity infrastructure project.

System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.








